Recently, we successfully conducted a POC for a Customer to migrate away from Azure Automation Credentials and Variables and everything to Azure KeyVault.
In this case, the Customer is using Azure Automation for Cloud Automation, an Azure VM as a Hybrid Worker for onPrem Automation, and local PS Script for that VM. So, we have three ways to execute and do the Automation, and the goal was to have a simple and secure way to get the Secrets from Azure Key Vault.
Authentication
So, the first and maybe most important part is the Authentication, we have three scenarios in who the PS and AA Runbooks are triggered and executed (Cloud, Hybrid, OnPrem) and wanted to have a”single” way to authenticate and get the secret Values via Azure Key Vault.
So, the Azure Automation Runbooks are executed as follows
- The Automation Account is executing the AA Runbook in the Cloud
- The Hybrid Worker is executing the AA Runbook on the Hybrid Worker
- local PS Scripts are executed on the Hybrid Worker
So, we are having 2 Identities that are executing the Automation
- The Automation Account is executing the AA Runbook in the Cloud
- A Hybrid Worker is executing AA Runbook and OnPrme PS Files
So let’s find a way to assign those two Identities permission to read our KeyVault; each of those identities has a “Managed Identity” in Azure, so let’s give the “Reader” Access to the Azure Key Vault.
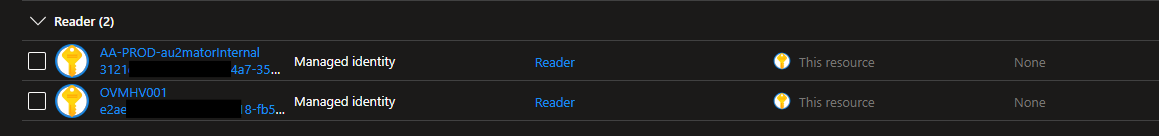
In the above Screenshot, the first entry is my Automation Account, and the second one is my Hybrid Worker, in this case with Azure Arc-enabled OnPrem Server.
There might be some more detailed and better documentation for this. Still, all the Managed identities we talked about have a separate endpoint to get the authentication token we can use in our PowerShell script to ” impersonate ” the managed identity to which we assigned the reader role above.
More Details can be found here:
- Managed Identity for Automation Account: Managed Identities – Azure App Service | Microsoft Learn
- Managed Identity for Azure Arc: Authenticate against Azure resources with Azure Arc-enabled servers – Azure Arc | Microsoft Learn
- Managed Identity for Azure VMS: Azure Instance Metadata Service for virtual machines – Azure Virtual Machines | Microsoft Learn
So, for this, we need to query a separate and different endpoint to get our access token, which we can then use to authenticate against the Azure KeyVault to get the secret value.
The example here shows how to use it with an Azure Arc-enabled Server. The Script on Github combines all three of them into a single Function.
Arc-enabled Server Example
For Azure Arc enabled Server, our Endpoint is this
$ResourceURL = "https://vault.azure.net/&api-version=2020-06-01"
$endpoint="http://localhost:40342/metadata/identity/oauth2/token?resource==$ResourceURL" When we call this endpoint, praise the result, and convert from JSON, we get the Access Token we can use further.
$global:AZKVResponse = [System.Text.Encoding]::Default.GetString((Invoke-WebRequest -Method GET -Uri $endpoint -Headers @{Metadata = 'True' } -UseBasicParsing).RawContentStream.ToArray()) | ConvertFrom-JsonSo, in the Global Variable, we now have tTokenken stored, and we are now building the header to get the Value of our Secret.
$token = $global:AZKVResponse.access_token
$Return = Invoke-RestMethod -Uri "https://$($KeyVaultName).vault.azure.net/secrets/$($SecretName)?api-version=7.1" -Method GET -Headers @{Authorization = "Bearer $($token)" }
return $return.valueIn this example, our $KeyVaultName is the unique name from our Azure Key Vault, and the $SecretName is the Name of the Secret you are trying to read.
Summary
In my opinion, and I am definitely not a Security Expert, but I think this might be the best and most secure way to store and use Secrets with Automation.
- Only the ManagIdentityity, so the Server or Automation Account has Access to the Key Vault.
- You are not forced to store Credentials locally for testing cause you can use the same code when executed in VS Code or in an Azure Automation Runbook
- Only humans who have access to the Automation Account or the Hybrid Server have access to the Secrets, which is easy to control.
- Many more…
GitHub
I stored a single function you can use on GitHub. We also created a Global Variable for tTokenken to reduce the number of Calls, as there is a throttling limit for the local endpoints here. There might be a better version in the future, but let’s look at the version on GitHub for details.
Repo: Seidlm/Microsoft-Azure: Azure Rest/Graph API Examples
File: Query Azure Key Vault.ps1
Michael Seidl aka Techguy
au2mate everything