In this post, we will create a Secret for an existing Azure Application Registration.
Graph API Basics
I did an MS Graph API Series some time ago to learn all the Basics that we will not cover in this Post
To learn more from Microsoft GRAPH API, see my Blog Series:
Part 1 – Authentication and Azure App – Use Microsoft Graph API with PowerShell – Part 1 » TechGuy
Part 2 – Oauth2.0 – Use Microsoft Graph API with PowerShell – Part 2 » TechGuy
Part 3 – First Powershell Script to get a Teams Lis and Walkthrough – Use Microsoft Graph API with PowerShell – Part 3 » TechGuy
Part 4 – this one – Use Microsoft Graph API with PowerShell – Part 4 » TechGuy
API Reference and Permissions
Read the following DOCS for more Details
https://docs.microsoft.com/en-us/graph/api/application-addpassword?view=graph-rest-1.0&tabs=http
Create an Azure App Reg with the following GRAPH API Application Permissions
- Application.ReadWrite.OwnedBy
- Application.ReadWrite.All
All done, then let’s see the Script
The Script
# Reference: https://docs.microsoft.com/en-us/graph/api/application-addpassword?view=graph-rest-1.0&tabs=http
#Application Permission:
#- Application.ReadWrite.OwnedBy
#- Application.ReadWrite.All
#Graph API Details
$MSGRAPHAPI_clientID = 'yourClientID'
$MSGRAPHAPI_tenantId = 'yourTenantID'
$MSGRAPHAPI_Clientsecret = 'yourSecret'
$MSGRAPHAPI_BaseURL = "https://graph.microsoft.com/v1.0"
#Enter Azure App Details
$AzureAppName = "TestApp1"
$SecretDescription="Secret1"
$SecretDurationInMonth=24
#Auth MS Graph API and Get Header
$MSGRAPHAPI_tokenBody = @{
Grant_Type = "client_credentials"
Scope = "https://graph.microsoft.com/.default"
Client_Id = $MSGRAPHAPI_clientID
Client_Secret = $MSGRAPHAPI_Clientsecret
}
$MSGRAPHAPI_tokenResponse = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$MSGRAPHAPI_tenantId/oauth2/v2.0/token" -Method POST -Body $MSGRAPHAPI_tokenBody
$MSGRAPHAPI_headers = @{
"Authorization" = "Bearer $($MSGRAPHAPI_tokenResponse.access_token)"
"Content-type" = "application/json"
}
#Get Appi from App Name
$GetIDfromName_Params = @{
Method = "GET"
Uri = "$MSGRAPHAPI_BaseURL/applications?`$filter=displayName eq '$AzureAppName'"
header = $MSGRAPHAPI_headers
}
$GetIDfromName_Result = Invoke-RestMethod @GetIDfromName_Params
#Add Secret to App
$AddSecretToAppReg_Body = @"
{
"passwordCredential": {
"displayName": "$SecretDescription",
"endDateTime": "$(Get-Date -format o (Get-Date).AddMonths($SecretDurationInMonth))"
}
}
"@
$AddSecretToAppReg_Params = @{
Method = "POST"
Uri = "$MSGRAPHAPI_BaseURL/applications/$($GetIDfromName_Result.value.id)/addPassword"
header = $MSGRAPHAPI_headers
Body = $AddSecretToAppReg_Body
}
$AddSecretToAppReg_Result = Invoke-RestMethod @AddSecretToAppReg_Params
#Secret
$AddSecretToAppReg_Result.secretText
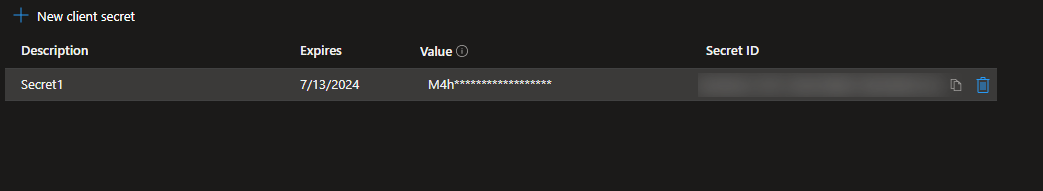
The Result
We now have a new Secret in our Azure Application Registration
and we can read the Secret in our PowerShell Script
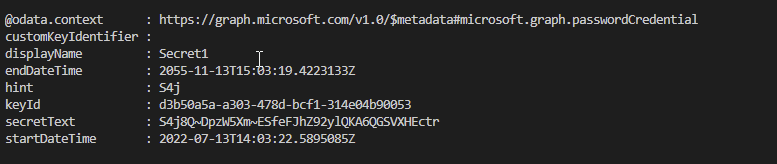
PRO TIP: with that code, you can also create Secrets with a higher Expire Date than 2 Years 😉
GitHub Repo
Make sure you get the Script from my Azure Github Repo: Seidlm/Microsoft-Azure: Azure Rest API Examples (github.com)
Name: Add Secret to Azure App Reg.ps1
Add Secret to an Azure Application Registration Self Service with au2mator
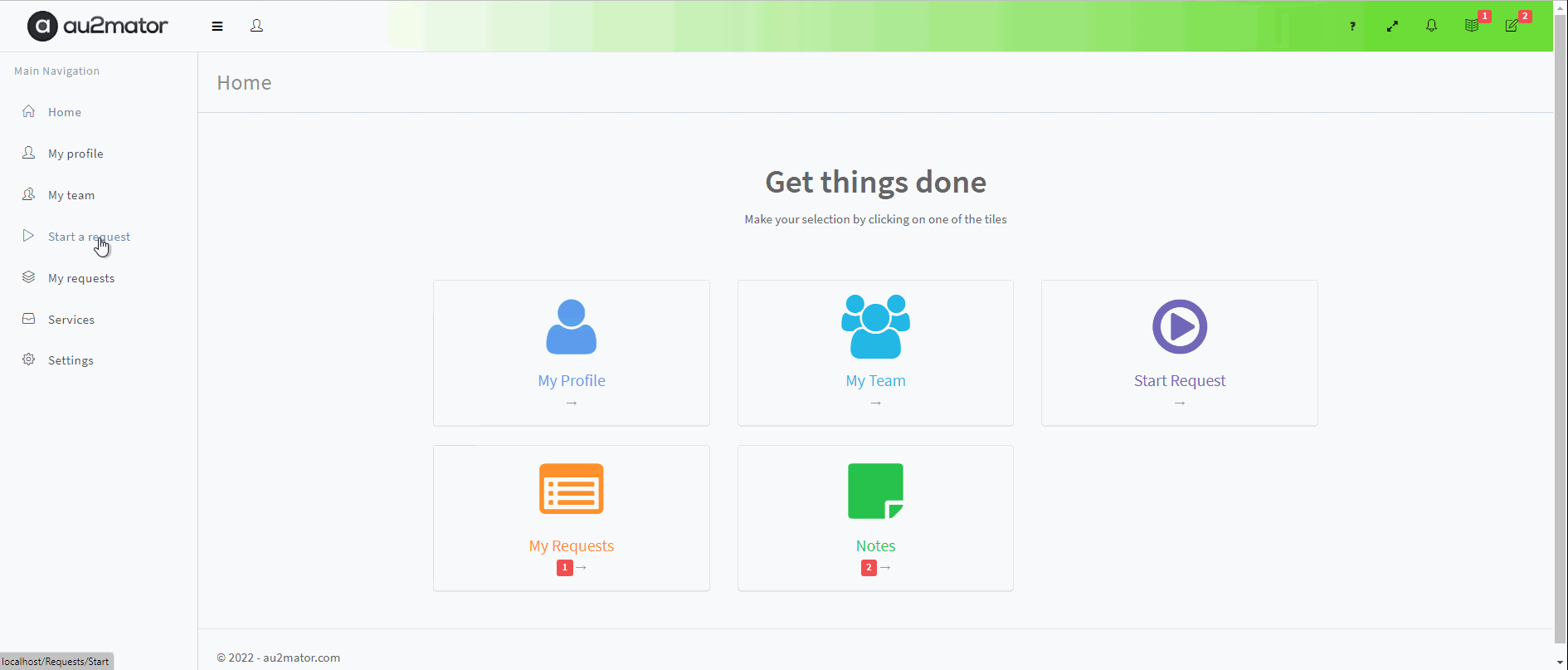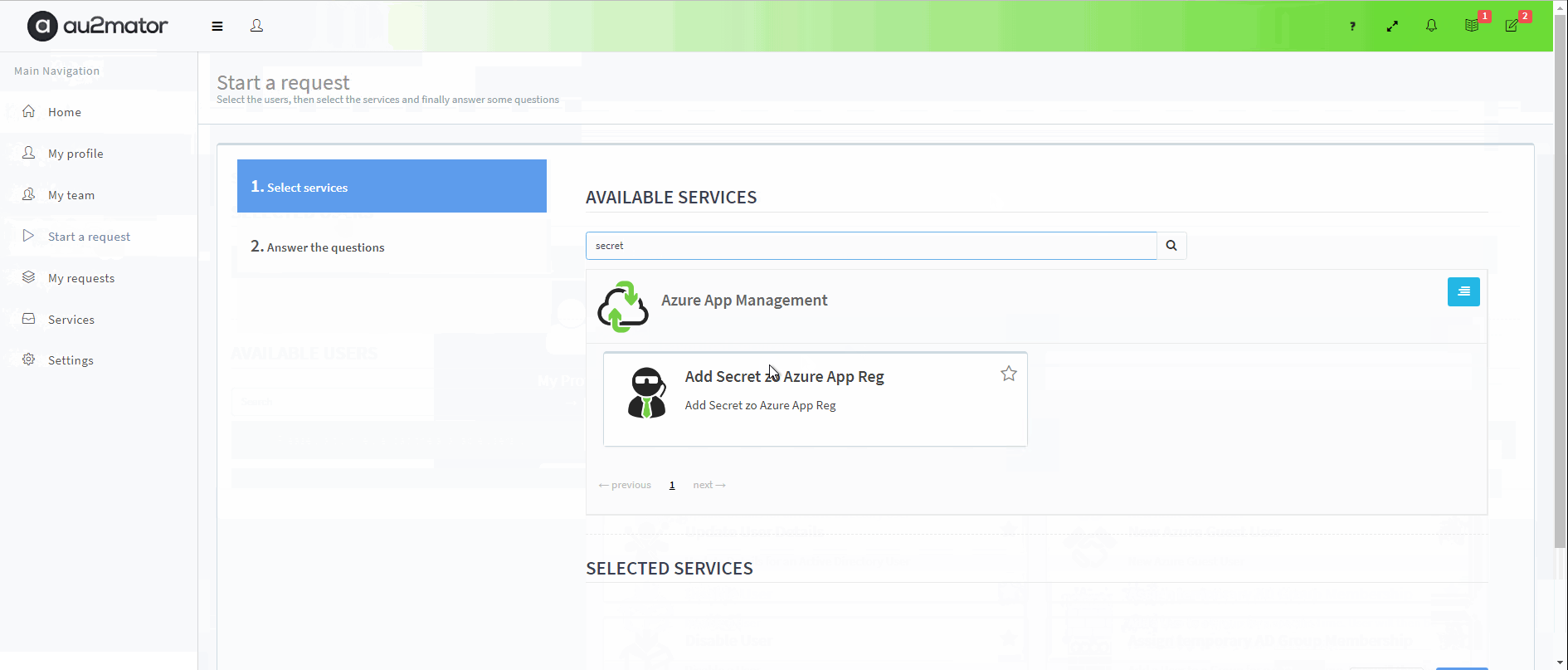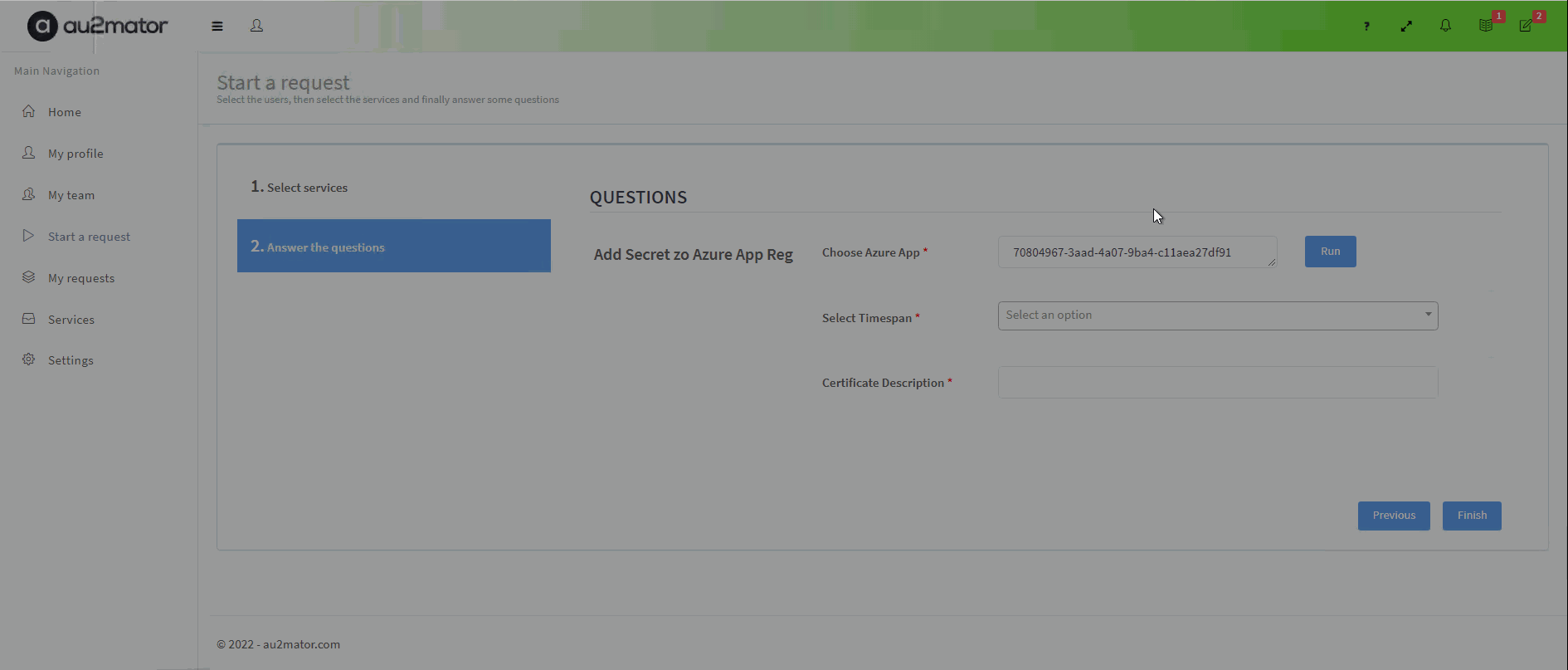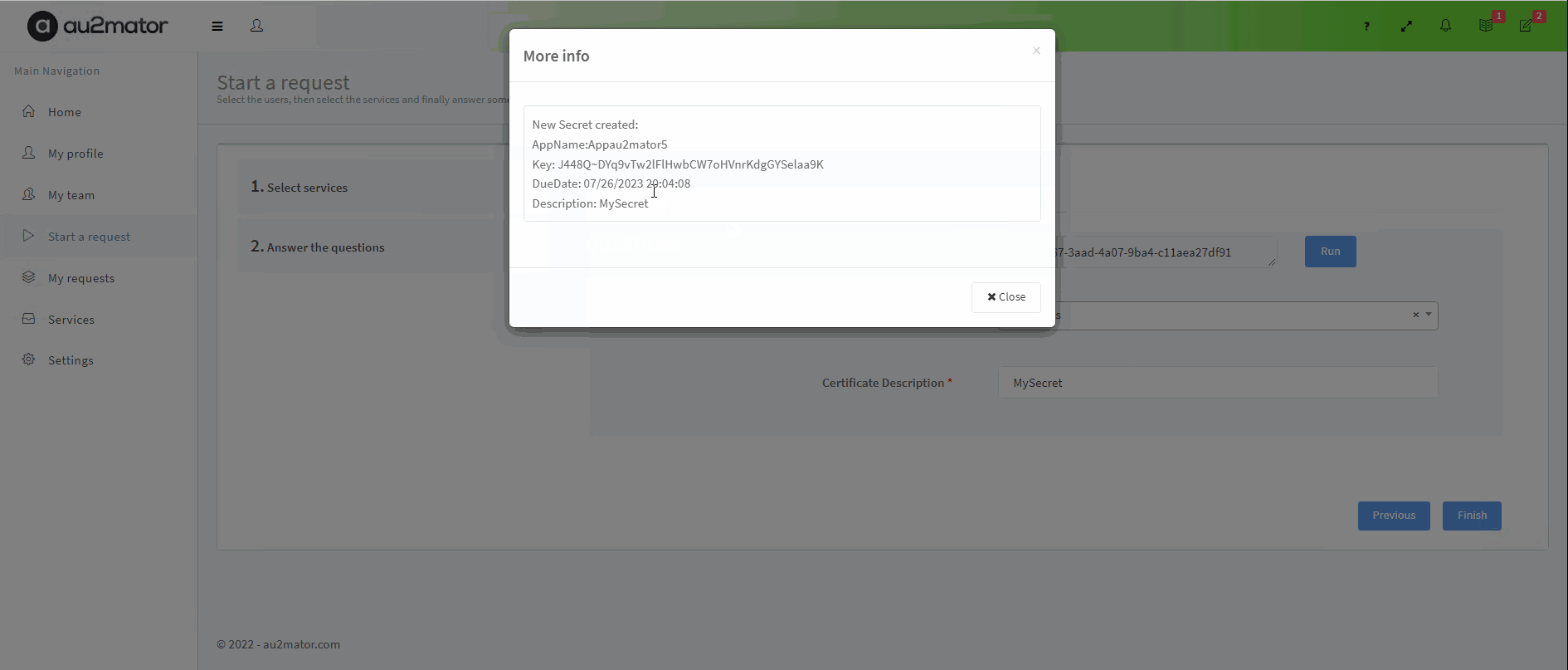
With au2mator Self Service Portal, you can create a Service and delegate the task to add a Secret to an Azure Application Registration.
Some of the Use cases❗
✔️Delegate the Secret Configuration of Azure App Registration
✔️Control your Secret Configuration outside Azure Portal.
✔️Mass add Secret to an Azure App Registration
✔️Approve or deny a Secret Request for an Azure App Registration
✔️Many more…
More Details: www.au2mator.com
Michael Seidl aka Techguy
au2mate everything